Why network administration service is important?
If you go to any manufacturer of firewalling devices, he will very quickly and reasonably prove that his company produces the most correct of the new generation, which are far superior to all their competitors. Moreover, he will not deceive you, at most - he will lie a little, as the concept of NGFW is not precisely defined (almost every manufacturer defines it in its own way), and whether there is a new generation of firewall features, or just numbers changed in the model name - it is not easy to figure it out.
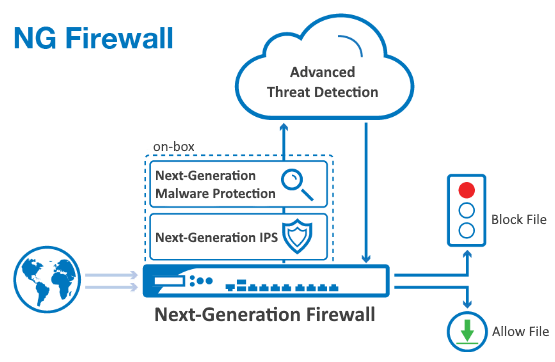
What features distinguish NGFW from the previous generation firewalls? First of all, it is the functionality to recognize and control applications. It also includes the following features:
Why is everyone switching to a next-generation firewall - Firewall: Next Generation (NGFW)? Because they don't sell any other kind!
- Intrusion Prevention (IPS);
- Deep packet inspection (DPI);
- URL filtering (Web reputation assessment);
- content and data format recognition;
- recognition and use of user and group accounts;
- SSL decryption and inspection.
You might say that you need to expand the list with features such as the ability to connect anti-virus engines, the availability of tools to protect against botnets, the implementation of a remote access gateway, support for virtual routers and security zones. I won't argue. Modern firewalls are not just devices implementing the rules of network communication between two networks, it's not even "two in one", it's 8-10 functions in one device. A sort of network security harvester.
But it is not important what functionality is in the device, but what functionality you need to solve your task and how well the implementation of these functions in a particular firewall device suits you.
How many firewall vendors do you think were in the upper right-hand square (the Leadership Square)? Two! We were pretty surprised, too. It seemed that with so many big names of manufacturers, with such a long and glorious history of networking equipment, including firewalls, you could expect much more. By the way, according to Gartner estimates, the situation in 2014 has not changed - the top right quadrant still has the same two companies: Check Point Software Technologies and Palo Alto Networks. Fortinet; Cisco and Juniper Networks were in the challenger quadrant (top left), and all other vendors huddled in the bottom left corner of the Niche Players. Judging by the fact that the Providers' square (bottom right) is empty, we do not expect any revolutionary changes in this area in the near future.
There is an opinion that NGFWs can protect against zero-day vulnerabilities and targeted attacks. In my opinion, the capabilities of NGFW in this part are greatly exaggerated.
We chose 4 companies for our testing, adding StoneSoft and McAfee to the previously announced leaders. At the time of the main tests, McAfee had already acquired Stonesoft, but both companies' firewall product lines were on the market.
I will not go into the technical details of the test, except to say that we were not interested in checking all functionality of the tested devices. We were mostly interested in the classic functionality, IPS implementation and fault tolerance. We have to understand that any sufficiently large company which pays attention to information security issues uses a whole set of specialized products to solve information security problems and all-in-one solutions are not really in demand. In addition, any additional functionality has a significant impact on the performance of the device. The same application detection and control functionality that makes writing firewall rules a lot easier and configurable requires a lot more resources than filtering by IP-addresses and ports. And if you enable IPS, SSL inspection and URL filtering on the same device, you should be prepared for the device performance (in terms of processed data flow) to "sag" several times.
The test results showed that all the devices were quite mature, and by and large any of the companies was able to present a device which could solve the problems we were facing. In such conditions, price indices, questions of integration into the existing IT infrastructure and IS system, the experience of existing IT specialists in working with the equipment of specific manufacturers come to the fore. It is worth paying attention to NGFW module licensing policy. It makes no sense to pay for the functionality you do not use, at the same time it is useful to be able to quickly get the required functions of the device if necessary, paying for them.
NGFW: the cure-all?
There is an opinion that NGFWs can protect against zero-day vulnerabilities and targeted attacks. In my opinion, the capabilities of NGFW in this part are greatly exaggerated.
Let me make a little analogy. You put up a sturdy, high and reliable fence in your summer house. It does a pretty good job of protecting you from the usual bullies, stray dogs and curious teenagers. But if someone sets a goal to break into your territory, he will do it. You can make a tunnel under almost any fence, you can climb over any fence with the right skills and equipment, and it is unlikely that the fence will stand up against heavy construction equipment. Finally, it is possible to get into the territory under the guise of an electrician or plumber, applying the method of social engineering.
When it comes to protection against zero-day vulnerabilities and targeted attacks we should consider NGFW as one of the elements of complex protection, which should be well integrated with the other elements of the system.
Certainly, at the moment, it is impossible to provide high efficiency of firewalling without appropriate cloud services - updated in real-time knowledge bases - and constant interaction of NGFW with such services.
An important question - who in your organization will administer the newly installed state-of-the-art equipment?
There is another important aspect I would like to consider. The classic version of the demilitarized zone (DMZ) implies the presence of two separate firewall devices to protect the demilitarized zone from attacks from the Internet and to protect the internal network from possible attacks from the DMZ. The functionality of modern NGFWs is aimed not only at limiting the capabilities of external attackers, but also at reasonably limiting the capabilities of an organization's employees when using modern IT services. Such functionality as recognition and control of applications, URL filtering, recognition and use of user accounts, decryption and inspection of SSL traffic is used primarily for analyzing outgoing traffic from the corporate network. Most IT and security professionals are accustomed to view firewalls as devices for analyzing incoming traffic. Going back to the classic scheme of DMZ organization, it turns out that NGFW should be installed on the external boundary of the DMZ to analyze incoming traffic, while for outgoing traffic analysis it is more appropriate to install NGFW on the internal boundary. If the budget allows, the issue is solved quite simply, otherwise you need to decide which of the tasks is a priority. In our company we use specialized proxy servers to analyze outbound traffic.
The question is not unimportant - who in your organization will manage the newly installed modern equipment? Even if the integrator who supplies you with the equipment is able to implement most of your wishes at the implementation stage (which is not always the case), the efficiency of the equipment may drop substantially in a relatively short period of time. Modern IT infrastructure is quite dynamic: new IT services appear regularly, business generates ideas at an alarming rate, internal and external intruders are not far behind. All of this will require an adequate change in NGFW settings, and it will be impossible to do so without trained staff.Moreover, not understanding how some mechanisms of NGFW work, network administrators, under the pretext of ensuring the health and productivity of the network, will turn off the "unnecessary" in their opinion functionality. Therefore, it is necessary to pay close attention to training and further maintenance of necessary qualification of IT-personnel. If you can not afford to maintain your own highly skilled professionals, you should think about outsourcing this functionality.Benefits of NGFWFinally, let us conclude by reiterating the advantages that NGFW has over traditional firewalls. Remember the two villages of Villaribo and Villabaggio from the Fairy detergent commercial? Villaribo is still poring over hundreds of classic Firewall (FW) rules, while Villabaggio has been celebrating for a long time, they have Firewall: Next Generation.In reality, of course, things are not as straightforward, but in NGFW many rules are much easier and more flexible than in classic FW. Some things, such as the use of peer-to-peer applications, are unrealizable in classic FW.And a much richer functionality, allowing to replace several security systems with a single device.

